

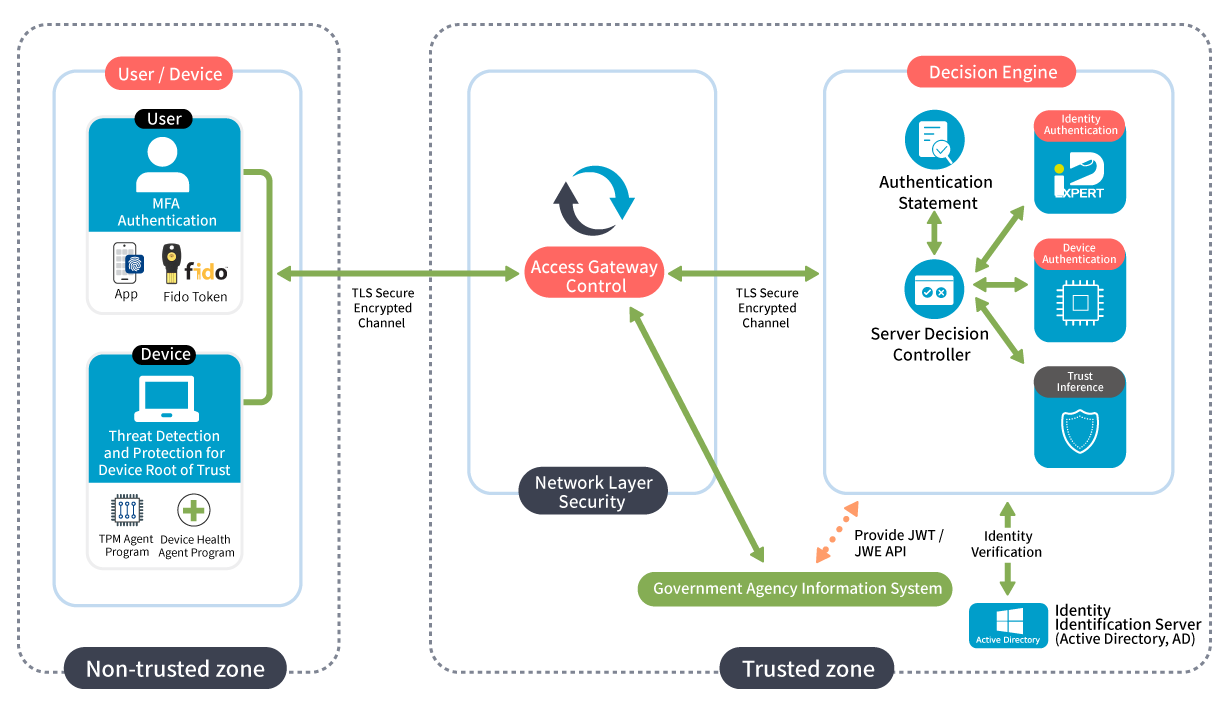
Network Control:
use network control devices to permit access based on trust levels or use access gateways-Reverse Proxy to allow access.
Authentication Statement:
Verify identity using strong authentication methods such as FIDO2. Check if the device's TPM has registered device certificates.
A Zero Trust architecture is built on the principle of "never trust, always verify" and requires repeated and multi-factor authentication to establish trust before accessing data. It has three core mechanisms:
Identity authentication: multi-factor identity authentication and identity authentication statement.
Device authentication: device authentication and device health management.
Trust inference: user context trust inference mechanism.
Taiwan government is promoting zero-trust network architecture and prioritizing the adoption of identity authentication. A-level government agencies, such as the Presidential Office, Executive Yuan, National Security Bureau, Ministry of National Defense, Ministry of Foreign Affairs, and the six municipal governments, are the first to implement zero-trust architecture. This initiative aims to promote the development of the zero-trust network security industry chain in Taiwan.
Identity authentication in 2022Device authentication in 2023Trust inference in 2024.
CHANGING's Identity Authentication products use diverse authentication mechanisms, are FIDO and OATH certified, and provide various applications and integration services. This ensures efficient identity verification in industries and government agencies, safeguarding information security and enhancing network defense.

authenticate and release after login with identity for obtaining authentication statement.
Agency information and communication system
second-stage authentication required through an authentication host prior to login.
Windows / Linux / Mac operating systems
VPN remote access
VDI remote office connection
Web page service
Mail system
