

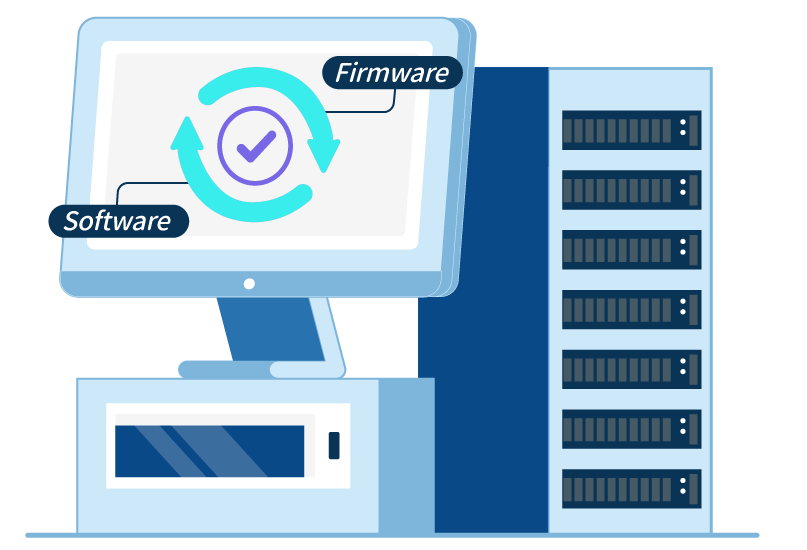
CHANGING IoT Security Solution ensures a "Zero Trust Network Architecture" by leveraging secure chip Trusted Roots (RoT) and device certificate PKI management. It verifies device legitimacy, prevents unauthorized software and firmware modifications, and ensures secure data transmission between devices. With this solution, users can enjoy the convenience of the IoT while ensuring a high level of security.
We utilize Infineon's OPTIGA™ TPM and OPTIGA™ Trust M secure chips, certified with Common Criteria EAL6+, for enhanced security. These chips have independent microprocessors and storage areas, ensuring physical isolation from the device's operating system and applications. With robust security features like secure boot, access control, and storage protection, they effectively safeguard against hacking attempts.

Devices utilize Bluetooth, WiFi, LoRaWAN, SIGFOX, or NB-IoT connections to establish internationally standardized encrypted channels. This ensures data confidentiality and employs symmetric and asymmetric encryption to protect device data.

Our certification authority system ensures secure loading of certificates into IoT devices, meeting the certification requirements of device manufacturers prior to deployment. Using unique device IDs and certificates, we guarantee the legitimacy of device deployment.

Our secure chips provide device firmware integrity checking, meeting the requirement for secure boot. During device startup, the firmware is automatically verified for any tampering. Only after successful verification, the device is allowed to start, ensuring increased security and reliability.
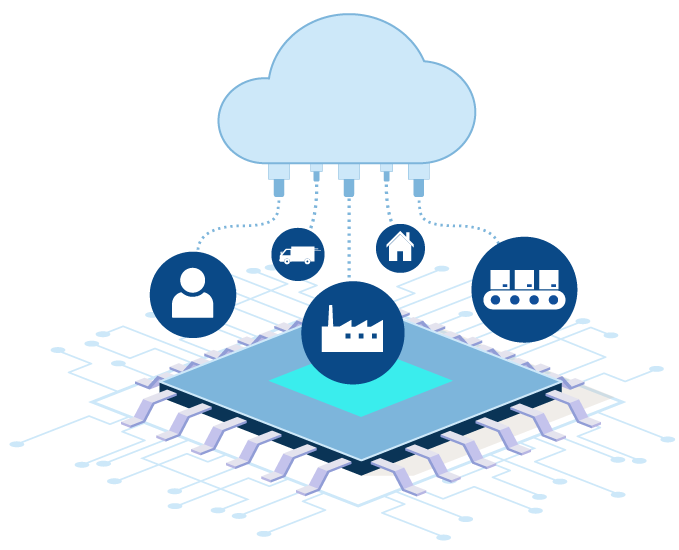
Seamlessly integrate with public cloud services such as AWS, Azure, and GCP, enabling fast and efficient deployment at scale.
Internet of
Things Cybersecurity
Improvement
Act (U.S.)
IEC 62443
(International
Industrial Control
Systems Security
Standard)
Cybersecurity
Resilience Act
(CRA, European)
Common Criteria Certified EAL6+ (high) hardware
Up to 10 kB user memory
PG-USON-10-2,-4 package (3 x 3 mm)
Standard (−25°C to +85°C) & Extended (−40°C to +105°C) temperature ranges
I2C interface with Shielded Connection (encrypted communication)
Security Function:
Device Identity
Digital Certificates & Signatures
Data Encryption & Key Derivation Function
Message Authentication Code (MAC)
TLS communication
Secure Boot
Secure Firmware Update